Let us for a moment assume that you have something important to tell over the phone. Maybe you’re a politician who wants to restrict your decisions to yourself and your closest partners?
All communication exposes information to risks. Do you know who’s listening in when you use your mobile? If the spy is cunning, you won’t even know if someone is eavesdropping. And do you know exactly who you’re talking to? Can you prove it? It’s easy for a hacker to take someone’s identity and pose to be this person. For someone with access to the operator’s network, eavesdropping is easy.
How to solve it? You can count on your opponents doing everything to find out your secrets. There are different types of opponents and different points where eavesdropping can take place.

Probably, someone who is a little adventurous has listened in to police radio? So did the villains, much to the annoyance of the police. Until the police force got Tetra radios, that are completely impossible to eavesdrop on for those who do not have the encryption password.
But ordinary people, politicians, researchers or business leaders cannot keep up with such luxuries. We will have to use regular mobile phones and the regular mobile network for the information transfer. You will just have to accept that there are lots of attack points where an enemy could break in to listen to the communication.
1 A Standard Phone
An ordinary, standard telephone has a number of programs (apps) pre-installed and the user builds on this himself, with several new ones over time. Open apps are those that the user can download from any app store. They can be bona fide or infected with spyware that sneaks into your phone.
An ordinary, standard telephone has a number of programs (apps) pre-installed and the user builds on this himself, with several new ones over time. Open apps are those that the user can download from any app store.
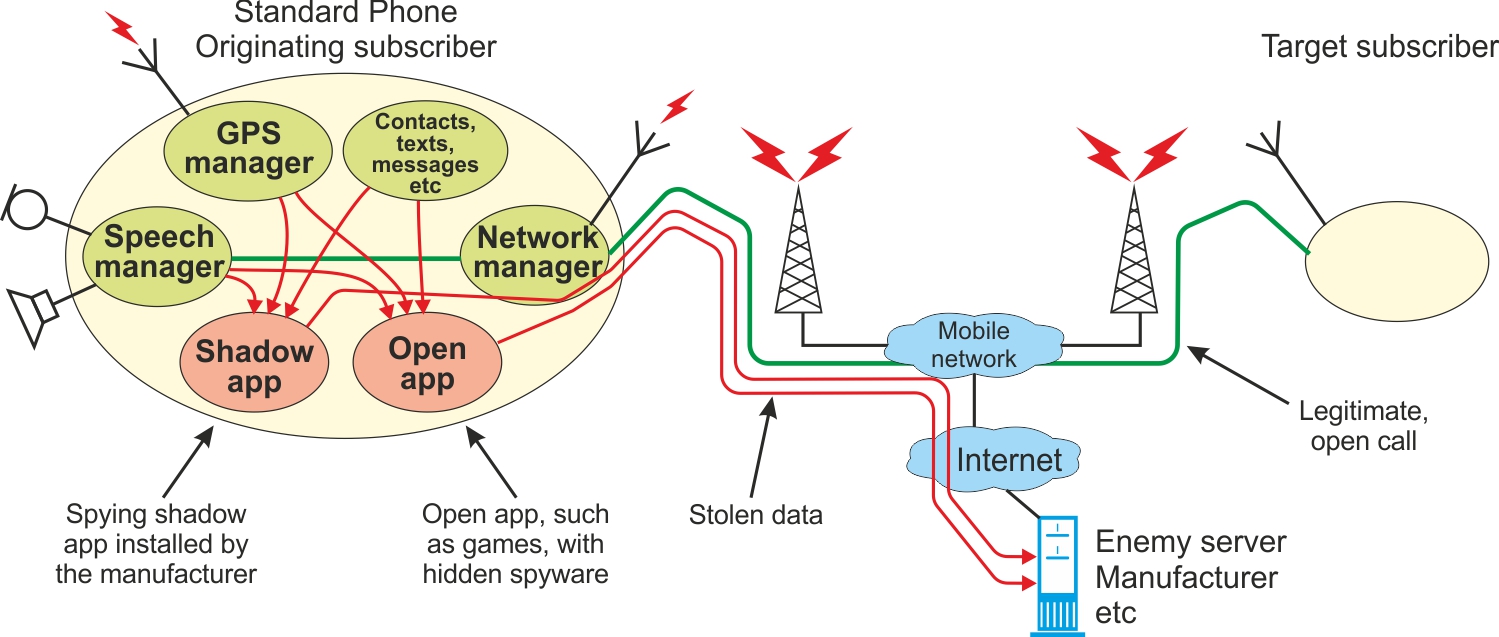
The originating subscriber in the above picture is the one who establishes the call, i.e. the caller. What the target subscriber does is in this case of little interest. The target device can be as safe as you like. The conversation may still be revealed. Actually, it is not even possible to know who the target subscriber is. It may be an impostor.
Shadow apps installed by the manufacturer do not need to care about the settings made by the user, but can communicate with the various handlers and retrieve voice data and GPS position etc. and send them on without restrictions.
Open apps, ie those you can download from app stores, can either obey the user’s settings or ignore them, albeit secretly, invisibly. They may also be infected with spyware that works (with or without) the app provider’s knowledge. Such problems are reported almost weekly.
The GPS position is a particular problem, because it may be of interest to an enemy from a blackmailing or tracking point of view. It has been found that even if the user turns positioning off in the phone’s menu, reporting to the phone manufacturer continues. Manufacturers have been forced to admit this at several occasions.
2 Phone with an Encryption App
Encryption apps are installed like any other app on your phone and can either encrypt your voice, texts or other textual messages. The encryption takes place during the transmission by the speech or text being taken care of by the encryptor and transmitted in another way than via the usual voice or SMS channel, ie as data traffic.
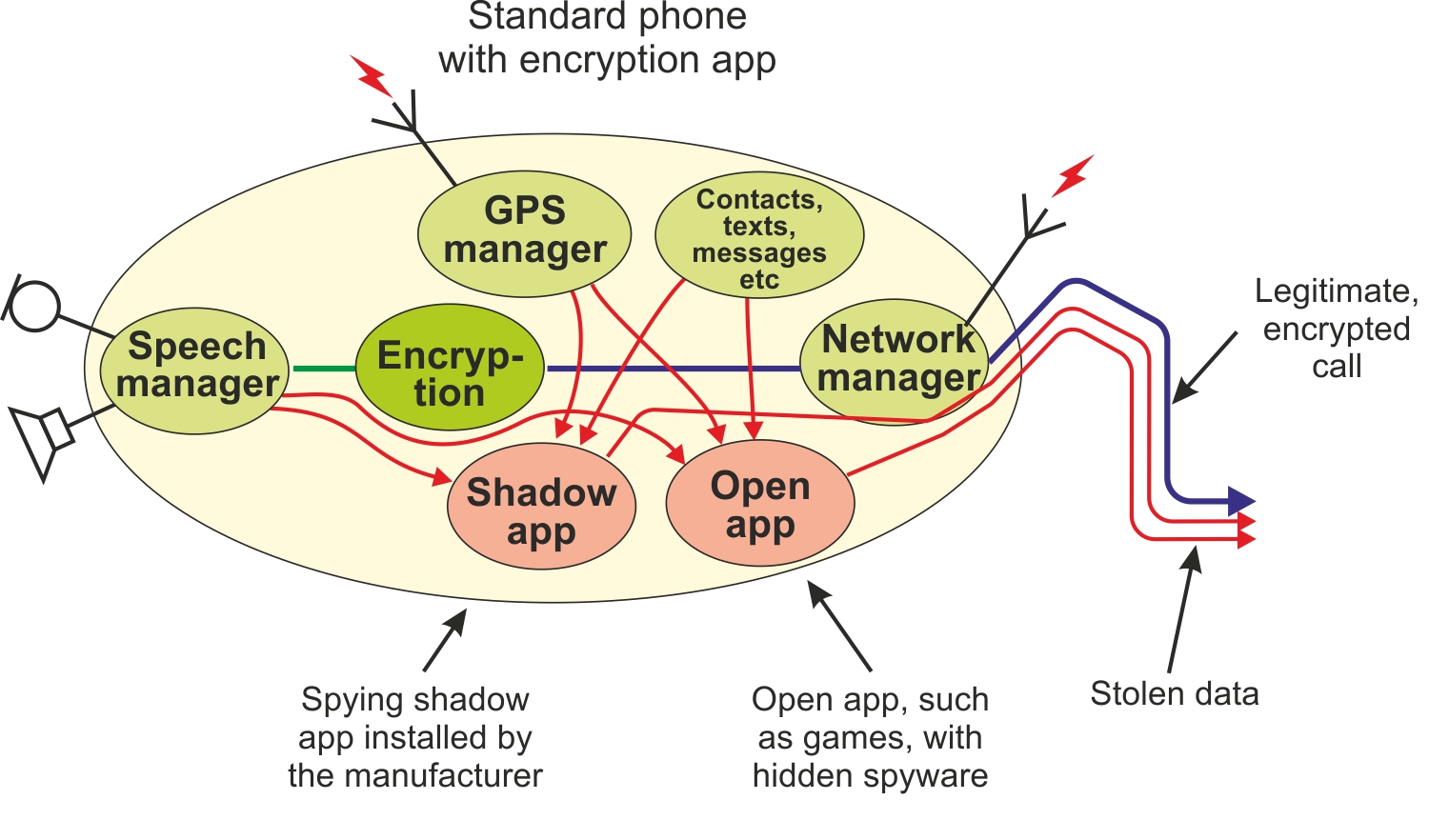
The picture shows how an app encrypts the speech, but alternatively it could be encrypting texts, pictures or the like. Because the speech is encrypted (blue line), it can no longer be sent over the mobile network’s voice channel, but is transmitted over the data channel, where it is simply accompanied by the stolen data.
Typical encrypted apps can be Telegram, Signal, Whatsapp, Wire and Imessage, but they all have the disadvantage that they live like any other app on the phone and cannot control how spy apps simultaneously access the plaintext. And if the supposedly “encrypted” app is in fact a spy app, you’re out of luck.
Other suspicious apps may still exist and do their “service” without you being able to control it.
So, encryption apps are thus more mirages than solutions.
3 Phone Utilising Safe Zones
Ordinary telephones are apparently not suitable for secure, encrypted traffic. The hardware is simply not set up to keep the plaintext secret. There are too many loopholes because all apps share primary memory and data storage.
Other suspicious apps may still exist and do their “service” without you being able to control it.

So-called red-black separation is a requirement of, for example, NATO, for the telephone to achieve the “secret” classification. The black side is the one that handles all network communication while the red side handles user interfaces and plain text calls. In the middle of them is the crypto circuit.
All plaintext information, such as speech, image, text or data, is digitized on the red side and encrypted by the crypto circuit before being transferred to the black side.
The disadvantage of this type of phones is that they are expensive, as they are not sold in large numbers and they require a central server for the distribution of new passwords and updates. In addition, it is required that both subscribers have the same type of telephone and agreed encryption algorithm and also the same, constantly updated passwords. This can be solved and is done daily in NATO, the EU’s internal circles and other organizations that want absolute secrecy.
A big advantage is that you can actually know who the target subscriber is.
4 No Apps!!
As you can see, apps are the worst culprits when it comes to eavesdropping. A secure phone has no apps. The only way to eliminate the problem of infected apps is to make it impossible to download apps from any app store.
You can modify a regular standard phone with Android OS so that it can achieve NATO classification “restricted”. The operating system has to be changed so that all programs execute in an isolated sandbox. Furthermore, unknown apps can be prevented from starting (so forget about games). In addition, an encrypted file system is needed, secured inside its own container with AES crypto with 256-bit key. The communication into the container is handled by VPN. However, since it is not possible to control which external devices are connected, or if the battery should “accidentally” be replaced with a fake battery with a built-in transmitter that forwards the telephone call to a third party, such a telephone can never be classified as “secret”.
5 Can you Buy a Secure Phone?
Yes you can. One example is the Swedish company SECTRA, which manufactures the Swedish Tiger telephone, which is set up with red-black separation and is approved by NATO for top secret communication.
As you can see, apps are the worst culprits when it comes to eavesdropping. A secure phone has no apps. The only way to eliminate the problem of infected apps is to make it impossible to download apps from any app store.

The concept also includes a “kill pill”, meaning that the phone will take its own life if it has been stolen and a harakiri order has been issued via the network. It is the same procedure as with Tetra radios, thereby increasing the security of the entire system.
6 But Would you Like Such a Phone?
It depends on how seriously you view your own work. You can not have privacy and fun, games and the Internet. Because the phone can not install apps, you can not play with it, only use it for voice, texts and file transfer and possibly photography.
It has been found that voice conversations are by far the best for communication in a stressful situation, especially in pressed and complex situations, compared to a written dialogue.
7 Who
Who would want to do this to a regular phone owner? It depends on what the purpose is.
If the purpose is to sell advertising or personal data, the interception can be performed by the telephone manufacturer, who places invisible shadow apps already during production. Advertising is profitable today.
If the purpose is to conduct political espionage, the spy organization may not have the opportunity to plant shadow apps but may rely on open apps. Games and video game apps are very popular and if they are infected with a spying part that works in the shadows and are attractive enough for the user (a lot of jokes, jumping people and flashing things) they can become so popular that the number of users can amount to hundreds of millions.
A third form is the completely open services on the Internet, such as social media, where the user voluntarily contributes their entire life, their opinions and images. The opinions are then sold on, either by the social network provider, or by someone who creates accessories for said social network. The purpose may be to influence opinion in any country ahead of, for example, a presidential election or withdrawal from the EU.
Against this, no encryption helps.
The concept also includes a “kill pill”, meaning that the phone will take its own life if it has been stolen and a harakiri order has been issued via the network.
MORE ARTICLES TO READ

Privacy
Integrity – Nag, Nag, Nag!
The problem with integrity is that it is a bit abstract and difficult to grasp as a con...

Hacks and Incidents
The Big Hacks that Shook the World
Hackers are international criminals. The Internet allows them to operate anywhere in th...
Hacks and Incidents
How to recognise phishing email
Do you think all the exciting emails that land in your inbox came from your friends or ...

Privacy
How to be invisible online
Taking just a few smart steps can aide your invisibility online and remember it’s impor...

Corporate news
Hidden24 top 10 rated in Tech Advisors VPN review
Tech Advisor's VPN review praised Hidden24’s simplicity of install, detailed graphical ...

VPN
VPN: The Ultimate Beginners Guide
VPNs are quite popular with everyone in today’s world. VPNs are quite popular with ever...